
Although DeFi has seen explosive growth, over $4.2B has been stolen over the past two years due to lacking security practices. This article explores trends and patterns behind these exploits, including the most common root causes. We explore steps that the DeFi ecosystem is taking to mitigate these risks, especially at scale. Lastly, we take a look at where the stolen money goes after an exploit, and how this is affected by the recent OFAC sanctions on money-mixer protocol Tornado Cash.
- Although DeFi has seen explosive growth, over $4.2B has been stolen from various protocols across 105 on-chain exploits. These vulnerabilities need to be analysed and mitigated for DeFi to mature into a credible and trustworthy industry.
- Cross-chain bridges and centralised exchange (CEX) wallets produce the largest hacks on average, while yield aggregators and lending protocols are exploited the most often. The largest exploits tend to be across multiple chains or on major ecosystem bridges.
- The most common root causes behind on-chain exploits can be broadly categorised as:
- Elimination of smart contract vulnerabilities is by far the most difficult of the three identified root causes, as the attack vectors are extremely varied. Tackling these risks at scale will most likely involve a combination of formal verification software to automate bug detection and DeFi security audits to review smart contracts holistically.
- Although future mitigation of risk is paramount, recovery of stolen funds is also important. While money-mixer protocol Tornado Cash was previously the most common escape route for hackers, it has since been sanctioned by the US Government after North Korean cyber-crime collective Lazarus Group was traced as a user. With the go-to method of cashing out dirty money shut down, exploiters are seeking new alternatives.
To date, the top 10 largest exploits are
- Exploits limit the growth of DeFi
- Trends and patterns
- Root causes
- Lessons learnt and future mitigation
- Where does the money go?
- Conclusions and key insights
DeFi has experienced substantial growth since the DeFi Summer of 2020, both in terms of user adoption and the number of protocols deployed. At one point, if all value across DeFi was aggregated, it would have represented the 31st largest bank in the US.
While number 31 sounds impressive for an industry that is essentially two years old, some argue that security practices have not kept pace with this explosive growth. Over the past two years, there have been over a hundred documented hacks and exploits across all of DeFi, adding up to $4.3B in lost assets. It’s hard to imagine what sort of unpleasantries regulators would be muttering under their breath if this ever happened to a TradFi bank.
As this pool of money grows larger in size, it will be harder and harder for DeFi to mature into a credible and trustworthy industry without addressing these security concerns. It is paramount to the future development of DeFi that these vulnerabilities are analysed and mitigated.
This article explores trends and key root causes behind these exploits, and then looks at how the industry is moving forward to address these risks. For the basis of this analysis, we will be using the incidents listed by DeFi exploit newsletter rekt, which keeps track of most major on-chain protocol hacks.
Cross-chain bridges most heavily impacted
Cross-chain bridges dominate the ranking of the largest exploits, including the three largest DeFi exploits yet: Ronin Network at $624M, Poly Network at $611M and Wormhole at $326M. The value secured by bridges is much higher than other types of protocols on average, with over $188M stolen per hack. This is because the nature of bridges require them to hold significant amounts of assets.
To bridge from one ecosystem to another, a user first deposits assets into a vault in the originating chain. These assets are locked up, after which equivalent assets are minted at the destination chain. The newly-minted assets function as an IOU, and can be burnt to unlock the assets on the originating chain. Since bridges hold massive amounts of these locked assets, the bridge protocols that control these vaults are highly popular targets for exploits.
CEX hot wallets, which also tend to hold large amounts of user funds, produce a similar pattern, with previous exploits including Bitmart at $196M, Ascendex at $77M and Kucoin at $45M.
While CEXs with strong security practices store most of their assets on cold wallets, some exchanges with less stringent policies leave a large portion of their assets on hot wallets, which are much more prone to exploits.
On the other hand, yield aggregators and lending protocols are the most common targets for exploits, but tend to have a lower amount lost per hack.
Largest attacks tend to be multi-chain
Many of the largest attacks take place across multiple chains, with cross-chain bridges and CEX hot wallets accounting for $2.2B in stolen funds, over 52% of the total exploited amount.
Following these large-scale multi-chain attacks, significant amounts of assets have also been lost on Ethereum, Ronin, Solana and Binance Smart Chain.
Ethereum and Binance Smart Chain have a long-standing DeFi ecosystem with consistently higher TVL than other chains. Both chains were also often the first ecosystems that new projects would launch on, which gave exploiters more potential vulnerabilities to experiment with. On the other hand, Ronin and Solana were the victims of major cross-chain bridge exploits, through which large portions of their ecosystem’s TVL were stolen.
Overall, bridges and CEXs tend to produce the largest losses per exploit, while yield aggregators and lending protocols were exploited more often. The largest exploits tended to be on projects that spanned multiple chains, or ecosystem bridges that hold a large portion of the chain’s total TVL.
In general, root causes can be sorted into three broad categories:
- Smart contract loopholes
- Compromised private keys
- Protocol frontend spoofing
Smart contract loopholes tend to be the most difficult risk to mitigate, as the attack vectors are extremely varied, and as such dominate in both metrics of exploited amount and number of exploits.
Compromised private keys generally produce a higher amount of loss per hack, as this is often the attack vector for larger pools of assets (such as bridges, CEX wallets or protocol treasuries).
Smart contract loopholes
Loopholes in smart contract code account for 73% of total hacks since Sep 2020. The category of loopholes vary widely and often depends on the type of protocol in question. For lending protocols or DEXs, exploits typically involve a combination of flash loans and/or price feed oracle manipulation, whereas for bridges this may involve more intricate ways of specifically targeting the underlying code.
A recent example is Inverse Finance, an Ethereum-based lending protocol which lost over $5.8M in Jun 2022. This particular exploit involved taking a large flash loan from AAVE to artificially push up the price of pre-deposited collateral, which allowed the hacker to drain the lending pool.
In addition to exploits perpetrated by malicious external parties, there are also self-imposed mistakes in smart contracts caused by the team themselves that led to substantial losses for protocols. Notable examples of this are Compound at $80M and Alchemix at $6.5M.
In both incidents, faulty smart contracts ended up distributing a larger-than-intended amount of treasury funds to users. In the case of Compound, the code in question was written by a community member, and was only peer-reviewed by other community members without direct involvement from the core team.
Compromised private keys
While compromised private keys produce the largest hacks on average at $91M per hack, it is ironically also the most easily avoided attack vector. Often used to secure cross-chain bridges or protocol treasuries, some of the most high-profile exploits have been due to stolen keys.
This boils down to two sub-causes: (1) the lack of operational security when storing keys and (2) the centralisation of key-holders. Although the exact methods used to steal private keys are still unknown, many speculate that these exploits are performed through social engineering spear-phishing attacks.
Taking Ronin Network as an example, a team member downloaded a PDF containing a generous fake job offer. The team’s internal network was compromised through this defective PDF, allowing the exploiter to steal 4 out of a total of 9 private keys. As the Axie Infinity DAO had also delegated their private key to the Ronin team, the exploiter was able to access the underlying funds through the 5 of 9 multisig.
While phishing attacks are ubiquitous, the team could have prevented the exploit by avoiding a single point of failure. This may include:
- Storing private keys in a more secure manner
- Using different devices across different platforms for storage
- Requiring more keys to activate the funds
Protocol frontend spoofing
Frontend spoofing is an attack vector that targets individual users rather than funds managed by the protocol. Typically this involves replacing the IP address of the real protocol website with a fake look-alike through methods like DNS cache poisoning.
The largest example of a frontend spoofing exploit is the BadgerDAO exploit in Dec 2021, through which the exploiter was able to siphon off $120M in user funds. BadgerDAO is a DeFi protocol that provides yield to wrapped versions of Bitcoin that had been bridged to Ethereum.
The hackers had managed to gain access to the team’s Cloudflare API key, after which they replaced the real Badger website with their own. Users then unknowingly approved unlimited token-spending caps to the fake address. After this, the hackers waited for more users to approve the spending limit until the cumulative amount was large enough for the hacker to pull the trigger and steal all the approved funds.
Frontend attacks may be difficult for crypto protocols to defend against alone, as the vulnerability often lies with third-party internet service providers. Aside from choosing a more reliable service provider, educating users to be cautious when giving unlimited token approval will also be important.
Some crypto wallets are now including an in-built feature that allows users to revoke token approval. As technology becomes more sophisticated, it is likely that security features will be abstracted into wallets themselves. For example, this may involve controlling token approvals, checking if a smart contract is the correct one before token approval, and more.
As smart contract loopholes are generally the most difficult vulnerabilities to mitigate while also making up the majority of lost TVL, this section will focus on how the industry is now tackling these risks.
We cover the two main methods of managing smart contract risk: automated formal verification and DeFi security audits. Together, they form a path toward scalable risk detection and mitigation for smart contracts.
Formal verification
Formal verification software is an automated method to detect smart contract bugs by proving that it meets a set of pre-determined rules. The verification software generates possible exploit scenarios against the smart contract, and flags out attack vectors that violate the rules.
As more protocols are deployed on-chain, there will be more smart contracts for exploiters to attack. With only so many pairs of hands available to manually review new contracts, this automated method of detecting smart contract bugs has been gaining popularity, especially as the underlying software grows increasingly sophisticated.
A prominent firm providing this formal verification software is Certora, which currently secures over $32B in DeFi TVL through their verification tool Certora Prover. Their users include industry-leading protocols such as AAVE, Compound, MakerDAO, SushiSwap and more.
The Certora Prover works by first collecting a set of requirements or rules that the user would like to test for their code. For example, the specification may be to test that the number of tokens that can be minted using this smart contract is within a certain limit.
After the proving is performed, the Certora team will generate a verification report based on the bugs found, listing the issues and mitigations ranked in order of importance from critical to low/recommendation.
Although formal verification may be an efficient way to identify bugged code, developers are still required to manually review and fix it. There have been recent efforts to automate vulnerability fixing entirely through generating iterative patches of code, although this technology still requires further development.
DeFi security audits
DeFi security audits provide a holistic view of all the risks and vulnerabilities that exist for a protocol. Audits are performed manually by DeFi audit firms, who then generate audit reports containing a list of issues and bug fix recommendations.
Audits tend to vary drastically in quality and rigorousness based on the audit firm. Notably, 32% of the exploits in the rekt leaderboard happened after the project had been audited.
Audits are also less scalable than automated approaches like formal verification. A combination of both approaches would be likely when securing DeFi at scale, especially as more protocols are deployed on-chain.
Although mitigation of future risk is paramount, the location and potential recovery of the stolen funds is also important.
Tornado Cash
Tornado Cash is a money-mixer protocol that provides payment privacy to users by obfuscating the trail of money. Users place a set amount of ETH into the protocol using address A and receive a key that acknowledges their input. Using this key, users can then withdraw the same amount of ETH using address B. As there are hundreds of users depositing and withdrawing every day, it is impossible to tell who had deposited the dirty funds.
Although Tornado Cash has a legitimate use-case in that it provides users with transaction privacy, it has also become one of the most common ways for exploiters to cash out their stolen loot. Some of the biggest DeFi hacks of all saw the hacker laundering their dirty funds through Tornado Cash.
North Korean cyber-crime collective Lazarus Group (who were behind the exploits of the Ronin Network and Harmony Protocol bridge) was eventually traced as a user of Tornado Cash. The US Government subsequently placed Tornado Cash on the OFAC sanctions list, blacklisting all wallets that had interacted with the protocol.
As Tornado Cash is an open-source project, the code could theoretically be forked to create a similar money-mixer protocol, but there were soon escalations in the severity of the sanctions. Not only was the Tornado Cash repository removed from GitHub, but the accounts of its core contributors were also deleted and one of the lead developers was arrested in the Netherlands. Wallets that had interactions with Tornado Cash were also banned from several major DeFi protocols.
The severity of the sanctions made some question if any future developers would risk implementing a Tornado Cash fork.
Alternative to Tornado Cash: Aztec Network
One potential alternative is Aztec Network, an Ethereum-based rollup that provides private transactions using zero-knowledge technology. Instead of storing user funds through account balances, Aztec tracks funds by issuing notes that represent the assets a user owns. These notes function as IOUs and can be redeemed for the underlying assets at a 1:1 ratio.
As Aztec notes are encrypted, outsiders would not be able to know the owner or the value of a note. Owners can redeem the underlying assets by generating a zero-knowledge proof for their note, proving that their ownership and the value contained.
However, the bridge to Aztec itself is fully transparent and relies on all users depositing fixed amounts to maintain anonymity. Following warnings from FTX to its users not to interact with Aztec, the network has announced that they will be implementing a 5 ETH deposit cap based on user IP addresses, leading some to question whether Aztec is prioritizing compliance over privacy.
Although DeFi is growing at incredible speed, $4.2B has been stolen over the past two years across 105 on-chain exploits.
While many security concerns are overlooked during this early hyper-growth stage, more stringent practices are required for DeFi to mature as an industry. If the relatively quick-fix of decentralizing the storage of private keys was applied early on, this alone would have prevented over $1.3B from being lost.
While attack vectors that focus on targeting smart contract loopholes may be harder to defend against, the industry is currently moving forward through a combination of automated bug detection and holistic security audits to protect the ecosystem at scale.
The authors of this content, or members, affiliates, or stakeholders of Token Terminal may be participating or are invested in protocols or tokens mentioned herein. The foregoing statement acts as a disclosure of potential conflicts of interest and is not a recommendation to purchase or invest in any token or participate in any protocol. Token Terminal does not recommend any particular course of action in relation to any token or protocol. The content herein is meant purely for educational and informational purposes only, and should not be relied upon as financial, investment, legal, tax or any other professional or other advice. None of the content and information herein is presented to induce or to attempt to induce any reader or other person to buy, sell or hold any token or participate in any protocol or enter into, or offer to enter into, any agreement for or with a view to buying or selling any token or participating in any protocol. Statements made herein (including statements of opinion, if any) are wholly generic and not tailored to take into account the personal needs and unique circumstances of any reader or any other person. Readers are strongly urged to exercise caution and have regard to their own personal needs and circumstances before making any decision to buy or sell any token or participate in any protocol. Observations and views expressed herein may be changed by Token Terminal at any time without notice. Token Terminal accepts no liability whatsoever for any losses or liabilities arising from the use of or reliance on any of this content.
Stay in the loop
Join our mailing list to get the latest insights!
Continue reading
Customer stories: Token Terminal’s Data Partnership with Linea
Through its partnership with Token Terminal, Linea turns transparency into a competitive advantage and continues to build trust with its growing community.
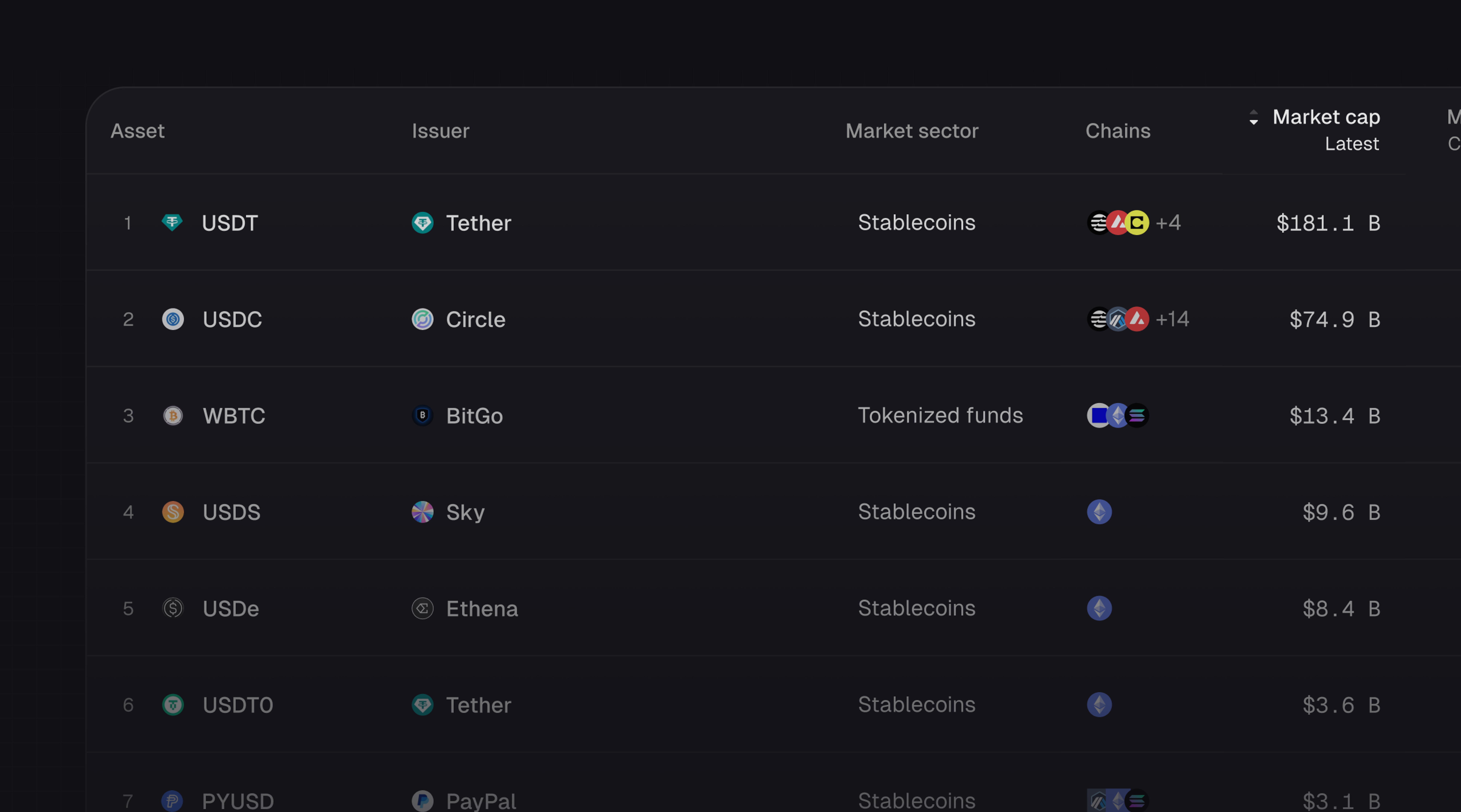
Introducing Tokenized Assets
Token Terminal is expanding its standardized onchain analytics to cover the rapidly growing category of tokenized real-world assets (RWAs) – starting with stablecoins, tokenized funds, and tokenized stocks.

Customer stories: Token Terminal’s Data Partnership with EigenCloud
Through its partnership with Token Terminal, EigenCloud turns transparency into a competitive advantage and continues to build trust with its growing community.