Research
Open-source services level the playing field for developers

Open-source services level the playing field for developers
All digital services today are powered by privately-owned databases. Crypto enables a new way to build and maintain databases. In crypto, digital services are built on top of decentralized database protocols operated by a community of network participants.
In only a few decades, the Internet went from a highly decentralized architecture to one controlled by a few powerful gatekeepers. This created monopolies, limited access for developers, and ultimately slowed down innovation.
Crypto protocols aim to break up this highly centralized architecture and provide developers a level playing field. Applications can again be solely built on open and permissionless protocols, which now have additional valuable features to them.
The current technology giants leveraged the decentralized Internet protocols to grow their businesses. Similarly, modern technology companies can now use crypto protocols as building blocks for novel applications, instead of having to rely on third-party access.
It is becoming increasingly clear that these building blocks continue to attract engineering talent globally. This post explains why.
Overview
This post is divided into six main sections:
- Cycles of Innovation in Information Technology
- History of the Internet
- The API Economy
- The Fundamentals of Crypto
- The Potential of Crypto
- Relevant Adoption Metrics
Cycles of Innovation in Information Technology
New computing platforms enable novel applications
Source: Chris Dixon, What’s Next in Computing (2016).
- New computing platforms enable novel applications.
- New computing platforms offer unique capabilities that enable developers and entrepreneurs to re-imagine entire industries and create new ones.
- We have seen many examples of this in information technology.
- In the 1980s, PCs enabled the creation of personal tools such as word processors, spreadsheets, and other desktop applications. The Internet connected these computers by offering a global information distribution network, turning prior tools into collaborative services such as search engines, social networks, and e-mail. Smartphones, in turn, made these services ubiquitous, adding a camera and GPS capabilities.
- Crypto is a new computing platform for Internet-native finance.
- Crypto enables financial transactions with email-like efficiency. These transactions are facilitated by collectively-owned open databases. As an Internet-native technology, crypto applications receive a global distribution from day one.
The next big thing always starts out looking like a toy
Source: Carlota Perez, Technological Revolutions and Financial Capital (2003).
- The next big thing always starts out looking like a toy.
- Each new technology goes through an investment phase before reaching mainstream utility. Speculation drives innovation and draws both talent and capital into an emerging market.
- A new computing platform always excels at one thing but is worse in most other ways.
- Initially, new technologies undershoot users’ needs which leads to them being widely dismissed as toys. Generally, people tend to underestimate the pace of innovation on new computing platforms. At first, smartphones were perceived as small and slow computers, yet today they are used for most things computing.
- We are still in the toy-phase of crypto.
- The novel capability in crypto is that it enables collective maintenance of open and global databases, and thus removes the need for trusted third-parties. These networks are still limited in their transaction processing capability. What is often disregarded is that crypto has attracted the same kind of developer interest as the Internet in its early days.
Open-source software compounds innovation
Source: Github Octoverse.
- Open-source software compounds innovation.
- The open-source software movement was started by a fringe group of researchers in the 1980s. Today, 97% of businesses use open-source software. Android is built on Linux, the most popular open-source operating system. In 2018, IBM acquired Red Hat for $33.4 billion and Microsoft acquired Github for $7.5 billion.
- Open-source software benefits the entire technology industry.
- The fact that anyone globally can contribute to and improve existing software results in fast-paced innovation. Developers can incorporate existing software into their products and services.
- Crypto enables the global coordination of open-source development.
- Instead of companies coordinating and economically incentivizing open-source development, crypto enables monetization of software directly from the protocol. Embedding economic incentives supercharge open-source development.
History of the Internet
The Internet started out as a research project, the aim was to create an open and decentralized communication network
Source: Brian McCullough, How the Internet Happened: From Netscape to the iPhone (2018).
- The Internet started out as a research project, the aim was to create an open and decentralized communication network.
- The initiative was funded by the government and academia. The goal was to create a communication network without any single points of failure. The commercial Internet was built on top of this network architecture.
- The Internet became ubiquitous because its underlying network was open and decentralized.
- Open communication standards provided a shared infrastructure for the transfer of information globally. Anyone could join, communicate with, or deploy applications to a global network in a permissionless manner.
- Crypto is an open financial communication network for the Internet.
- Crypto enables global financial infrastructure without single points of failure. Anyone can use and deploy financial applications on top of a shared infrastructure. An open financial infrastructure enables permissionless innovation.
Early Internet protocols were mere communication channels
Source: Wikipedia, Internet Protocol Suite.
- Early internet protocols were mere communication channels.
- Protocols define communication standards between computers on the Internet. These protocols are used in all Internet communication to ensure fast and reliable transfer of information. Different types of information require different protocols: web requests (HTTP), email (SMTP), voice (VoIP), etc.
- Internet protocols are limited because they cannot store state.
- Internet protocols move information but cannot store it. This means communication can never build on previously sent information. Communication through these protocols lacks context.
- Before crypto, any meaningful activity on the Internet has required third-parties.
- The ability to record information (state) is a prerequisite for building Internet applications. To date, privately-owned companies have maintained databases for communication through Internet protocols.
Internet protocols required privately-owned third-party databases to reach their full potential
Source: Ben Thompson, Aggregation Theory (2015).
- Internet protocols required privately-owned third-party databases to reach their full potential.
- All Internet services rely on the ability to store data from prior activity. For example, it would be impossible to maintain a record of a user’s social network without access to previously established contacts.
- Entrepreneurs saw great potential in aggregating data.
- Privately-owned databases keep a record of the activity on the Internet. This data is filtered and sorted to create user-friendly applications. The better the user experience, the more users are attracted to a service, leading to more data being gathered. This pattern resulted in a virtuous cycle whereby a handful of technology companies became data monopolies.
- Crypto protocols store data in collectively-owned databases.
- Crypto protocols can be used as open databases for applications. Instead of companies aggregating the data, it is aggregated at the protocol-level and becomes shared infrastructure. Applications and users can tap into and benefit from the same data store.
Data monopolies became the gatekeepers of the Internet
Source: NFX, The Network Effects Manual: 13 Different Network Effects (2018).
- Data monopolies became the gatekeepers of the Internet.
- What started out as a decentralized network, effectively became a network controlled by a handful of large technology companies. Google and Facebook now have a direct influence of over 70%+ of all Internet traffic. Due to that influence, startups spend almost 40 cents of every VC dollar on Google, Facebook, and Amazon to acquire customers.
- Users find the most value plugging into existing services with prior network effects.
- Large technology companies (GAFA) are able to offer their users access to a network of billions of relevant counterparties (users, suppliers, customers, service providers, etc.). In addition, they are able to offer an unparalleled user experience because of the user data they have accumulated.
- Lack of competition stifles innovation on the Internet.
- Gatekeepers used to attempt to compete, and this competition kept the Internet market diverse. Today, most of these companies dominate their respective parts of the Internet. As a result, consumers are losing diversity of choices.
The lack of a native payment layer set constraints on possible business models on the Internet
Source: Connie Chan, When Advertising Isn’t Enough (2018).
- The lack of a native payment layer set constraints on possible business models on the Internet.
- Today, companies often focus either on the attention economy or the wallet economy. The former are often data marketplaces that emphasize engagement and monetize via advertisements (Facebook, Twitter, Snapchat), whereas the latter is often content and product marketplaces that monetize via transactions (Amazon) and/or subscriptions (Spotify, Netflix). The main sources of revenue for Internet companies have become concentrated.
- Existing payment infrastructure does not support frictionless payments.
- Currently, the brick-and-mortar payment methods that have been ported on to the Internet make small and continuous payments infeasible. Seamless payments would give product developers more accurate data on what users value. In addition, traditional payment rails offer poor security guarantees.
- Traditional payment rails hurt the user experience on the Internet.
- An increasing number of advertisements have made many applications and services difficult to use. Extreme targeting in advertising hurts privacy and the software is often malicious. Subscription-based revenue models lock users into overly broad service offerings. Users are forced to sign up for monthly or annual subscription plans — many forget to cancel their subscriptions once they quit using the product or service.
The API Economy
The leading technology companies are platforms
Source: Scott Kupor, On Startups, Platforms, and Innovation (2019).
- The leading technology companies are platforms.
- They are two-sided marketplaces that connect users and services. Platforms thrive on network effects and user-generated content. For service providers, platforms enable cost-efficient customer acquisition. For users, platforms curate and provide access to high-quality service providers.
- Platforms have capital-efficient business models.
- Uber is the most valuable taxi company without owning a single car. Airbnb is the biggest hospitality service without owning any real estate. Spotify is a marketplace for music where all the content is generated by artists. Youtube is the largest video streaming service without any proprietary content.
- Platforms rely on network effects and user-generated content without rewarding their users.
- The typical lifecycle of a platform is to raise venture capital funding to acquire users and boost network effects. In turn, a platform’s users make the service more compelling for new service providers and users. Once the platform reaches critical mass, companies are able to extract rent on the platform activity in perpetuity.
A platform’s relationship to third-party complements changes over time
Source: Chris Dixon, Why Decentralization Matters (2018).
- A platform’s relationship to third-party complements changes over time.
- Successful platforms tend to follow a similar pattern in their adoption. As platforms move up the adoption S-curve, their power over users and third-parties grows steadily. When they hit the top of the S-curve, their relationship with network participants changes from cooperation to competition.
- Centralized platforms start as recruiters and end up as value extractors.
- In the beginning, platforms need to recruit users and third-party complements like developers, businesses, and media organizations to make the service more valuable to users. Once a platform reaches critical mass, the natural path to grow the business is to compete with complements for market share.
- Platforms are naturally inclined to stifle innovation.
- For third-party complements, the transition from cooperation to competition makes it difficult to build sustainable businesses and makes entrepreneurs weary of building on centralized platforms. A recent high profile example of this kind of platform risk is the Spotify vs. Apple case, in which Apple is accused of unfairly promoting its own music service in the App Store.
Applications rely on multiple other service providers’ API access for their core features
Source: Martin Casado, The World Through an API (2018).
- Applications rely on multiple other service providers’ API access for their core features.
- Applications do not operate in isolation. Instead, they are often connected to the database APIs of multiple outside service providers.
- Modularity is mutually beneficial for technology companies.
- Many functionalities are often impractical to build from the ground up, which is why companies tend to rely on other service providers for many of their core features.
- Crypto protocols replace traditional APIs by provisioning a cheaper and more reliable service.
- API access is costly to maintain. For example, Uber paid $58 million for the right to use Google Maps from 2016 to 2018. An API provider’s unilateral right to change data access rights creates an inherent platform risk for third-party application developers. When building on top of crypto protocols, developers do not have to worry about sudden changes to data access rights. Open infrastructure eliminates platform risk for third-party developers.
The Fundamentals of Crypto
Crypto protocols are new Internet infrastructure
Source: Emre Tekisalp, Understanding Web 3 — A User Controlled Internet (2018).
- Crypto protocols are new Internet infrastructure.
- Crypto protocols add open data layers to the current Internet protocol suite. Business logic previously performed by companies can now be directly programmed into the protocol. Crypto protocols are owned, maintained, and operated by a network of online participants instead of a centralized company.
- Crypto protocols are permissionless platforms for developers to build on.
- Developers can now build their application on a shared data layer through APIs that are not controlled by a centralized company. Applications and users have equal access to a shared data store.
- Crypto protocols provide sophisticated building blocks for developers.
- A shared programmable data layer makes developing applications faster and more capital-efficient. In addition, it removes the platform risk inherent to centralized platforms.
Crypto has grown from an obscure forum post to an institutional asset class in ten years
- Crypto has grown from an obscure forum post to an institutional asset class in ten years.
- The Bitcoin protocol specification was initially published in 2008. The first significant venture capital investments into crypto were made in 2013. The launch of Ethereum in 2015 attracted the attention of many developers and opened up the design space for crypto applications.
- The Internet was supposed to have a native payment layer.
- Similar to the error “404 Not Found” for web pages, there exists a “402 Payment Required” error in the Internet error-code specifications. The founders of the Internet expected a digital payment layer to be integrated in the 1990s but were unable to solve the technical challenge of maintaining a global database without a trusted third-party.
- Crypto turns payments into Internet packets.
- Similar to how the Internet enabled permissionless information transfer, Bitcoin enables permissionless value transfer. Any Internet-connected device can freely participate in the Bitcoin network.
The Bitcoin protocol provides economic incentives for its participants to maintain a global and open database
Source: Satoshi Nakamoto, Bitcoin: A Peer-to-Peer Electronic Cash System (2008).
- The Bitcoin protocol provides economic incentives for its participants to maintain a global and open database.
- Network participants compete for the right to verify transactions in the Bitcoin network. By updating and maintaining the database honestly, participants are rewarded with Bitcoin.
- The Bitcoin protocol is a solution for bypassing intermediaries.
- Without the need for trusted third-parties, money on the Internet becomes secure and transactions across borders become effortless.
- The traditional financial infrastructure has inherent friction.
- All banks maintain their own internal transaction databases. Bitcoin offers an alternative by functioning as a single, shared, and open transaction database. As a result, money can now be sent and received across the globe with email-like efficiency.
The Potential of Crypto
Ethereum enables the creation of smart contracts
Source: Ethereum, A Next-Generation Smart Contract and Decentralized Application Platform (2014).
- Ethereum enables the creation of smart contracts.
- Smart contracts are common goods embedded in the Ethereum blockchain. Their pre-programmed functionalities are available for anyone to interact with in exchange for payment.
- Developers realized the potential of programmable money.
- Bitcoin can be thought of as a calculator, capable of performing simple functions, whereas Ethereum is more like a computer, capable of executing arbitrarily complex transaction logic.
- Smart contracts expanded the design space for crypto applications.
- Smart contracts are building blocks for applications and can be deployed on a global and open data layer. Since software is simply human-thought encoded into a machine-readable format, any idea a developer is able to formalize within these constraints can be made into an application.
Ethereum’s programmability led to explosive growth in smart contract development
Source: dApp.com.
- Ethereum’s programmability led to explosive growth in smart contract development.
- Open financial instruments (for lending, derivatives, exchange, etc.) are financial programs that can be interacted with, without trusted third-parties. Open marketplaces for core Internet infrastructure (storage, computation, video transcoding, content delivery, etc.) enable any user to provide and consume compute resources directly from other network participants. Non-fungible tokens represent globally portable unique digital information, such as gaming items or online identities.
- The crypto space provides developers and technology entrepreneurs with unrivaled opportunities.
- Developers have been given the tools to rebuild financial and Internet infrastructure from the ground-up. The magnitude of an application’s potential impact, combined with the newfound ability to monetize open-source software, has led to an increasing number of developers entering the space.
- The next-generation of Internet applications will be built on top of crypto protocols.
- The unique capabilities offered by crypto protocols enable a new class of Internet applications to be built. Similar to how entrepreneurs built new businesses on top of open Internet protocols, crypto protocols enable developers to re-imagine existing industries and build entirely new ones.
Decentralized applications utilize crypto protocols for their core features
Source: https://www.argent.xyz.
- Decentralized applications utilize crypto protocols for their core features.
- Similar to how traditional Internet companies rely on third-party API access, applications built on crypto protocols access similar functionalities without the associated platform risk.
- Developers can build without platform risk.
- Without having to rely on third-party APIs, developers can minimize their infrastructure risks. Unlike the current application development environment, crypto protocols create economic incentives that discourage data siloing. Instead, developers have economic incentives to create protocols that can be easily integrated with other protocols and applications — this in order to increase traffic and usage of their own protocol.
- Modularity and composability of crypto protocols result in fast-paced innovation.
- As developers are able to deploy applications on top of existing backend infrastructure, creating a compelling user experience becomes the main differentiator between applications. For example, a decentralized banking service can be built efficiently by creating a user interface that is connected to crypto protocols that provide relevant financial primitives, such as exchange, lending, and/or derivatives.
Augur: a protocol for prediction markets
Source: Augur, a Decentralized Oracle and Prediction Market Platform (2018).
- Augur: a protocol for prediction markets.
- The Augur protocol allows anyone to create, trade, and verify the results of prediction markets. Prediction markets can be used to bet on events, forecast the probability of future events, and hedge against risks.
- Augur provides cheap and global access to any financial market.
- Anyone with an Internet connection can participate in and create Augur markets. The protocol contains built-in economic incentives that encourage network participants to operate markets with minimal fees.
- Decentralized applications build on top of Augur’s features and provide a user interface for consumers.
- Decentralized applications curate and filter interesting markets to their users. Since trade execution and settlement both occur directly in the protocol, users do not have to rely on a trusted third-party to custody their assets in order to participate in Augur markets. Instead of relying on the security of a single company, users benefit from the global network security of the underlying protocol.
Value creation and value capture will shift from company shares to protocol tokens
Source: Joel Monegro, Fat Protocols (2016).
- Value creation and value capture will shift from company shares to protocol tokens.
- Crypto protocols are able to perform many of the value-adding functions previously performed by centralized companies.
- Crypto protocols aggregate value by charging fees for the functionality they provide.
- As crypto protocols enable the creation of better services (cheaper, faster, and more secure) for consumers, they are likely to capture a majority of all financial activity that occurs on the Internet.
- Crypto represents the biggest revolution in information technology since the Internet.
- Crypto protocols may become ubiquitous in the same way as TCP/IP or SMTP, protocols that all of today’s major Internet applications rely on. However, in contrast to TCP/IP or SMTP, it is possible to own shares of crypto protocols and benefit financially from all of the traffic they facilitate in the future.
Relevant Adoption Metrics
Monthly downloads of the Ethereum development framework Truffle
Source: Truffle.com, Developer Suite Downloads.
Daily transaction fees paid on the Ethereum network
Source: Etherscan.io, Ethereum Daily Gas Used.
Daily transaction count on the Bitcoin network
Source: Blockchain.com, Bitcoin Confirmed Transactions per Day.
Number of newly registered users per year on Coinbase
Source: Alistair Milne, Coinbase Data.
ETH locked in decentralized finance protocols
Source: Mike McDonald, ETH Locked in Defi.
Venture capital funding into crypto
Source: Coindesk, Blockchain Venture Capital.
The value held in different types of monies
Source: Marketwatch, All the Money in the World in One Chart (2017).
Global Internet, smartphone, and e-commerce penetration
Source: Benedict Evans, the End of the Beginning (2018).
Institutional involvement
Sources: Bloomberg, Goldman-Backed Circle Agrees to Buy Crypto Exchange Poloniex; Fortune, Andreessen Horowitz Pours $300 Million into Crypto Fund; Bloomberg, Yale Invests in Crypto Fund That Raised $400 million; Fidelity Digital Assets; Bakkt.
The authors of this content, or members, affiliates, or stakeholders of Token Terminal may be participating or are invested in protocols or tokens mentioned herein. The foregoing statement acts as a disclosure of potential conflicts of interest and is not a recommendation to purchase or invest in any token or participate in any protocol. Token Terminal does not recommend any particular course of action in relation to any token or protocol. The content herein is meant purely for educational and informational purposes only, and should not be relied upon as financial, investment, legal, tax or any other professional or other advice. None of the content and information herein is presented to induce or to attempt to induce any reader or other person to buy, sell or hold any token or participate in any protocol or enter into, or offer to enter into, any agreement for or with a view to buying or selling any token or participating in any protocol. Statements made herein (including statements of opinion, if any) are wholly generic and not tailored to take into account the personal needs and unique circumstances of any reader or any other person. Readers are strongly urged to exercise caution and have regard to their own personal needs and circumstances before making any decision to buy or sell any token or participate in any protocol. Observations and views expressed herein may be changed by Token Terminal at any time without notice. Token Terminal accepts no liability whatsoever for any losses or liabilities arising from the use of or reliance on any of this content.
Stay in the loop
Join our mailing list to get the latest insights!
Continue reading
Customer stories: Token Terminal’s Data Partnership with Linea
Through its partnership with Token Terminal, Linea turns transparency into a competitive advantage and continues to build trust with its growing community.
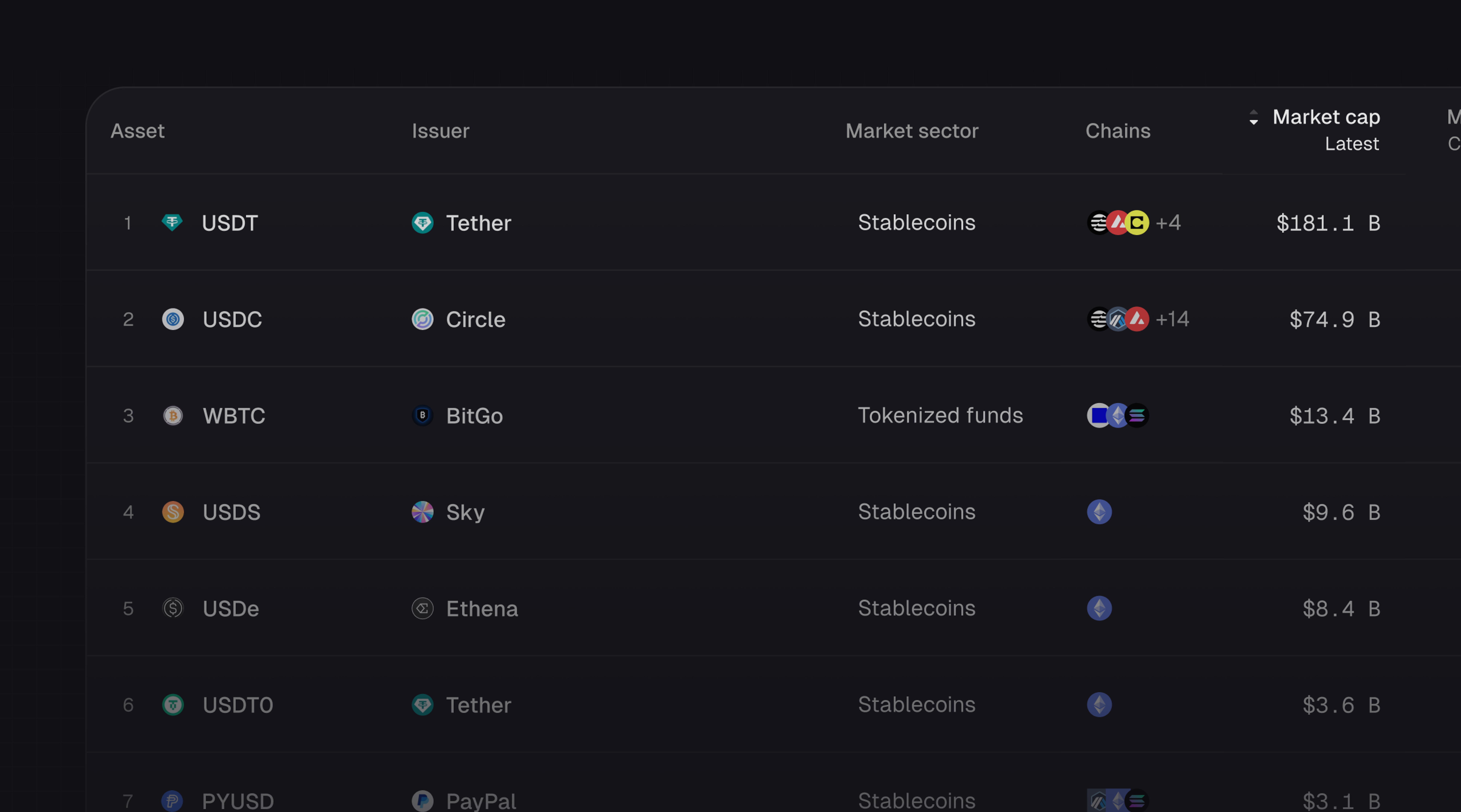
Introducing Tokenized Assets
Token Terminal is expanding its standardized onchain analytics to cover the rapidly growing category of tokenized real-world assets (RWAs) – starting with stablecoins, tokenized funds, and tokenized stocks.

Customer stories: Token Terminal’s Data Partnership with EigenCloud
Through its partnership with Token Terminal, EigenCloud turns transparency into a competitive advantage and continues to build trust with its growing community.